In the era of digital transformation, healthcare organizations are rapidly transitioning their operations to digital platforms. While this shift brings efficiency and streamlined processes, it also raises crucial concerns about the security of sensitive patient data.
Traditional methods of data protection are no longer sufficient. As digital repositories fill with confidential information, robust solutions are necessary. This is where data de-identification plays a significant role. This emerging technique is a critical strategy for safeguarding privacy without hindering the potential for data analysis and research.
In this blog post, we will delve into the details of data de-identification. We will explore why it could be the shield that helps protect valuable data.
What is Data De-identification?
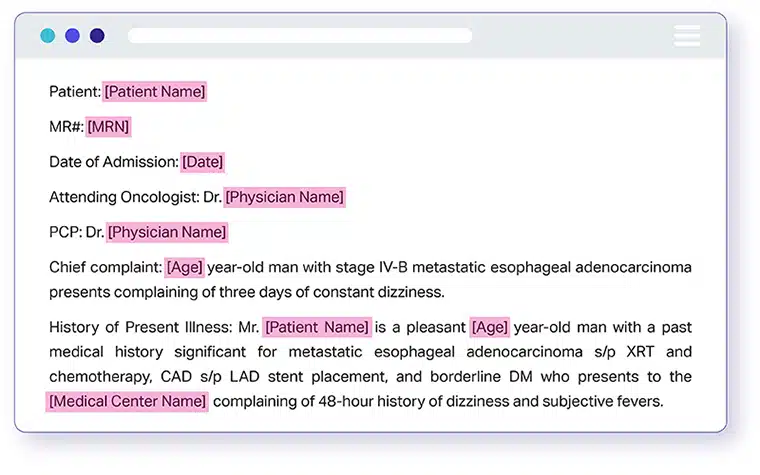
Data de-identification is a technique that removes or alters personal information from a data set. This makes it challenging to link data back to specific individuals. The aim is to protect individual privacy while retaining the data’s usefulness for research or analysis.
For instance, a hospital might de-identify patient records before using the data for medical research. This ensures patient privacy while still enabling valuable insights.
Some of the use cases of data de-identification include:
- Clinical Research: De-identified data allows for the ethical and secure study of patient outcomes, drug efficacy, and treatment protocols without violating patient privacy.
- Public Health Analysis: De-identified patient records can be aggregated to analyze health trends, monitor disease outbreaks, and formulate public health policies.
- Electronic Health Records (EHRs): De-identification protects patient privacy when EHRs are shared for research or quality assessment. It ensures compliance with regulations like HIPAA while maintaining data usefulness.
- Data Sharing: Facilitates the sharing of healthcare data among hospitals, research institutions, and governmental agencies, enabling collaborative research and policy-making.
- Machine Learning Models: Utilizes de-identified data to train algorithms for predictive healthcare analytics, leading to improved diagnostics and treatments.
- Healthcare Marketing: Allows healthcare providers to analyze service utilization and patient satisfaction, aiding in marketing strategies without risking patient privacy.
- Risk Assessment: Enables insurance companies to assess risk factors and policy pricing using large datasets without individual identification.
How Does Data De-Identification Work?
Understanding de-identification begins by distinguishing between two types of identifiers: direct and indirect.
- Direct identifiers, such as names, email addresses, and social security numbers, can unmistakably point to an individual.
- Indirect identifiers, including demographic or socio-economic information, might identify someone when combined but are valuable for analysis.
You must understand which identifiers you want to de-identify. The approach to securing the data varies based on the identifier type. Several methods exist for de-identifying data, each suitable for different scenarios:
- Differential Privacy: Analyzes data patterns without exposing identifiable information.
- Pseudonymization: Replaces identifiers with unique, temporary IDs or codes.
- K-Anonymity: Ensures that the dataset has at least “K” individuals sharing the same set of quasi-identifier values.
- Omission: Removes names and other direct identifiers from datasets.
- Redaction: Erases or masks identifiers in all data records, including images or audio, using techniques like pixelation.
- Generalization: Replaces precise data with broader categories, like changing exact birth dates to just the month and year.
- Suppression: Deletes or substitutes specific data points with generalized information.
- Hashing: Encrypts identifiers irreversibly, eliminating the possibility of decryption.
- Swapping: Interchanges data points among individuals, such as swapping salaries, to maintain overall data integrity.
- Micro-aggregation: Groups similar numerical values and represent them with the group’s average.
- Noise Addition: Introduces new data with a mean of zero and positive variance to the original data.
These techniques offer ways to protect individual privacy while retaining the usefulness of the data for analysis. The choice of method depends on the balance between data utility and privacy requirements.
Methods of Data De-identification
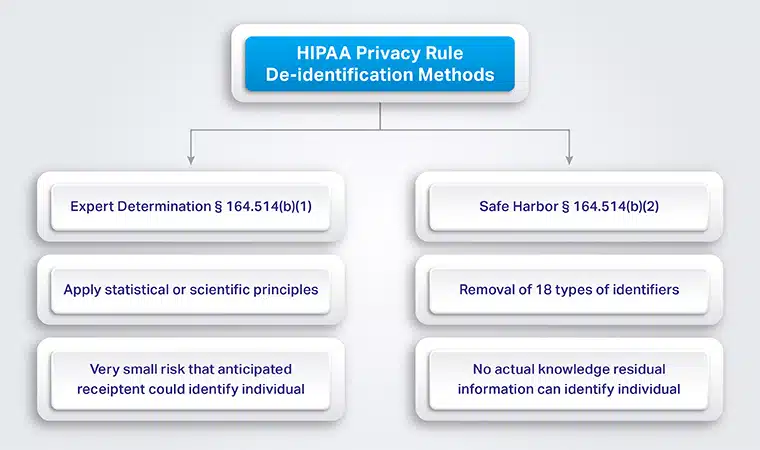
Data de-identification is crucial in healthcare, especially when complying with regulations like the HIPAA Privacy Rule. This rule uses two primary methods to de-identify protected health information (PHI): Expert Determination and Safe Harbor.

Expert Determination
The expert determination method relies on statistical and scientific principles. A qualified individual with adequate knowledge and experience applies these principles to assess the risk of re-identification.
Expert determination ensures a very low risk that someone could use the information to identify individuals, alone or combined with other available data. This expert must also document the methodology and results. It supports the conclusion that there’s minimal risk of re-identification. This approach allows flexibility but requires specialized expertise to validate the de-identification process.
The Safe Harbor Method
The safe harbor method provides a checklist of 18 specific identifiers to be removed from the data. This comprehensive list covers names, geographic data smaller than a state, elements of dates related to individuals, and various types of numbers like phone, fax, social security, and medical record numbers. Other identifiers like email addresses, IP addresses, and full-face photographs are also on the list.
This method offers a more straightforward, standardized approach but might result in data loss that limits the data’s usefulness for some purposes.
After applying either of these methods, you can consider the data de-identified and no longer subject to HIPAA’s Privacy Rule. That said, it’s crucial to understand that de-identification does come with trade-offs. It leads to information loss that could reduce the data’s utility in specific contexts.
Choosing between these methods will depend on your organization’s specific needs, available expertise, and the intended use of the de-identified data.
Why Is De-Identification Important?
De-identification is crucial for several reasons It can balance the need for privacy with the utility of data. Have a look at why:
- Privacy Protection: It safeguards individuals’ privacy by removing or masking personal identifiers. This way, personal information remains confidential.
- Compliance with Regulations: De-identification helps organizations comply with privacy laws and regulations like HIPAA in the US, GDPR in Europe, and others worldwide. These regulations mandate personal data protection, and de-identification is a key strategy to meet these requirements.
- Enables Data Analysis: By anonymizing data, organizations can analyze and share information without compromising individual privacy. This is particularly important in sectors like healthcare, where analyzing patient data can lead to breakthroughs in treatment and understanding of diseases.
- Fosters Innovation: De-identified data can be used in research and development. It allows for innovation without risking personal privacy. For example, researchers can use de-identified health records to study disease patterns and develop new treatments.
- Risk Management: It reduces the risk associated with data breaches. If data is de-identified, the information exposed is less likely to harm individuals. It reduces the ethical and financial implications of a data breach.
- Public Trust: Properly de-identifying data helps maintain public trust in how organizations handle personal information. This trust is crucial for the collection of data necessary for research and analysis.
- Global Collaboration: You can easily share de-identified data across borders more easily for global research collaborations. This is especially relevant in fields like global health, where sharing data can accelerate the response to public health crises.
Data De-Identification vs Sanitization, Anonymization, and Tokenization
Sanitization, anonymization, and tokenization are different data privacy techniques that you can use apart from data de-identification. To help you understand the distinctions between data de-identification and other data privacy techniques, let’s explore data sanitization, anonymization, and tokenization:
| Technique | Description | Use Cases |
| Sanitization | Involves detecting, correcting, or removing personal or sensitive data to prevent unauthorized identification. Often used for deleting or transferring data, like when recycling company equipment. | Data deletion or transfer |
| Anonymization | Removes or alters sensitive data with realistic, fake values. This process ensures that the dataset cannot be decoded or reverse-engineered. It uses word shuffling or encryption. Targets direct identifiers to maintain data usability and realism. | Protecting direct identifiers |
| Tokenization | Replaces personal information with random tokens, which may be generated by one-way functions such as hashes. Although tokens are linked to original data in a secure token vault, they lack a direct mathematical relationship. It makes reverse engineering impossible without access to the vault. | Secure data handling with reversibility potential |
These methodologies each serve to enhance data privacy in different contexts.
- Sanitization prepares data for safe deletion or transfer so that no sensitive information is left behind.
- Anonymization permanently alters data to prevent the identification of individuals. This makes it suitable for public sharing or analysis where privacy is a concern.
- Tokenization offers a balance. It protects data during transactions or storage, with the possibility of accessing the original information under secure conditions.
The Benefits And Drawbacks Of De-Identified Data
We have data de-identification because of the benefits it provides. So, let’s talk about the benefits of using de-identified data:
Benefits of De-Identified Data
Protects Confidentiality
De-identified data safeguards individual privacy by removing personal identifiers. This ensures that personal information remains private, even when used for research.
Supports Healthcare Research
It allows researchers to access valuable patient information without compromising privacy. This supports advancements in healthcare and improves patient care.
Enhances Data Sharing
Organizations can share de-identified data. It breaks down silos and fosters collaboration. This sharing is crucial for developing better healthcare solutions.
Facilitates Public Health Alerts
Researchers can issue public health warnings based on de-identified data. They do this without revealing protected health information, thus maintaining privacy.
Drives Medical Advances
De-identification enables the use of data for research that leads to healthcare improvements. It supports innovation partnerships and the development of new medical treatments.



